Here is a new article series using Phoenix Contact’s Security Router FL MGUARD 1105! Cyber security is one of the essential issues in our FA industry today.
We will start with a brief introduction and setup of the Security Router FL MGUARD 1105 and the concept of security.
Come on, let’s enjoy FA.
Reference Video
Cybersecurity…
Cybersecurity requires protecting components, networks, and systems from unauthorized access and ensuring data integrity. To do so, organizational and technical measures must be put in place to protect network-enabled devices, solutions, and PC-based software.
Recommendation
✓Isolate components and systems from the public network
Avoid integrating components or systems into a public network and use a VPN (Virtual Private Network) if you need to access components or systems via a public network.
✓Firewall Settings
Configure firewalls to protect the network and the components and systems integrated into the network from outside influences. Use firewalls to segment networks or isolate controllers.
✓Stop unused communication channels
Disable unused communication channels (SNMP, FTP, BootP, DCP, etc.) among the components in use.
✓Consider Defense-in-Depth in System Planning
When protecting components, networks, and systems, it is not enough to simply implement measures that have been considered in isolation; a Defense-in-Depth strategy would do well to encompass several coordinated measures involving operators, integrators, and manufacturers.
✓Restrictions on access rights
Restrict access to components, networks, and systems to individuals whose authorization is strictly necessary, and suspend unused user accounts.
✓Secure Access
For starters, make a mental note to change your default login information after the first startup. Also, use a secure password that reflects complexity and longevity.
Its password should be changed according to the rules applicable to its use and use a password manager with a randomly generated password.
Also, whenever possible, use a central user management system to simplify user management and login information management.
✓Re-secure access to remote access using a secure access path
Use secure access routes such as VPN (Virtual Private Network) or HTTPS for remote access.
✓Enable security-related event logging
Enable security-related event logging in accordance with security guidelines and legal requirements for data protection.
✓Use the latest firmware version
Ensure that the firmware of all devices used is always up-to-date.Also check the devices in use and security advisories for published security vulnerabilities.
✓Use the latest security software
Install security software on all PCs to detect and eliminate security risks such as viruses, Trojan horses, and other malware, and ensure that you are always using the latest database.
✓Conduct regular threat analysis
Threat analysis should be conducted on a regular basis to determine if the measures taken for your components, networks, and systems are still providing adequate protection.
✓Secure access to SD card
Devices with SD cards need to be protected against unauthorized physical access; SD cards can be read at any time with a conventional SD card reader; if SD cards are not protected from unauthorized physical access (e.g., by using a secure management cabinet), sensitive data can be accessed by anyoneaccess.
Ensure that the SD card cannot be accessed by unauthorized persons and that data cannot be recovered when the SD card is destroyed.
FL MGUARD 1000?
The FL MGUARD 1000 series is an industrial security router with a built-in stateful packet inspection firewall.It provides high data throughput and helps to decentralize and protect production cells and individual machines from unauthorized operation.
NAT router
As a router or gateway, the device connects to a subnet or network zone.Each network zone is assigned a separate IP address through which the device can be accessed from the network.
NAT features (IP masquerading, 1:1 NAT, port forwarding) make it easy to integrate separate machines (PLCs) or multiple subnets with the same IP settings into an existing network without having to change the IP settings of the machines or subnets.
Security by Design
All mGuard devices feature proven mGuard security technology and are designed from the ground up to meet network security requirements.The devices use a strong firewall.System and network services are hardened.
Vulnerabilities – quickly closed (PSIRT)
All end-of-life components are continuously monitored through the PSIRT process (Product Security Incident Response Team).Any security gaps detected or reported are immediately analyzed and closed if necessary.
For more information, please refer to this site.
https://www.phoenixcontact.com/de-de/service-und-support/psirt?cpn=murl_psirt&murl=psirt
Layout
This is the Layout of FL MGUARD 1105 used in this article.
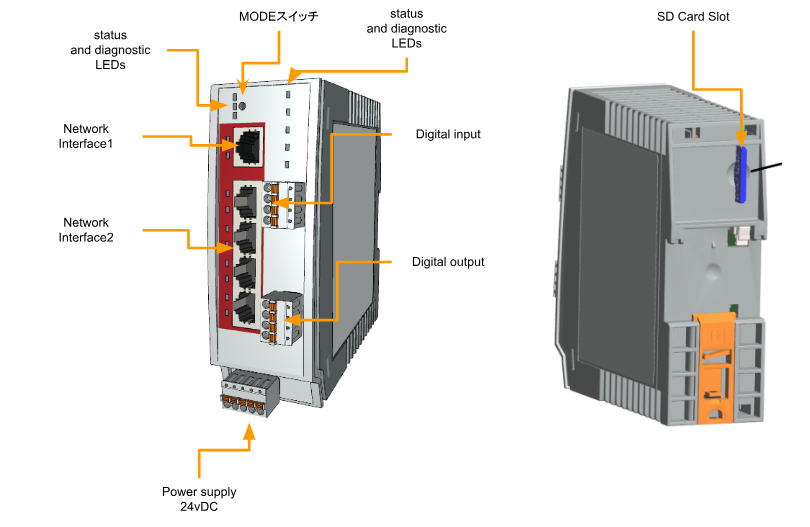
Factory settings
In the factory configuration, the device is configured as follows
XF1
If there is a DHCP server in the network, an IP address will be assigned automatically.IP masquerading (NAT) is also applied to all routed data packets leaving the device via network interface XF1 (downstream of netzone 1).
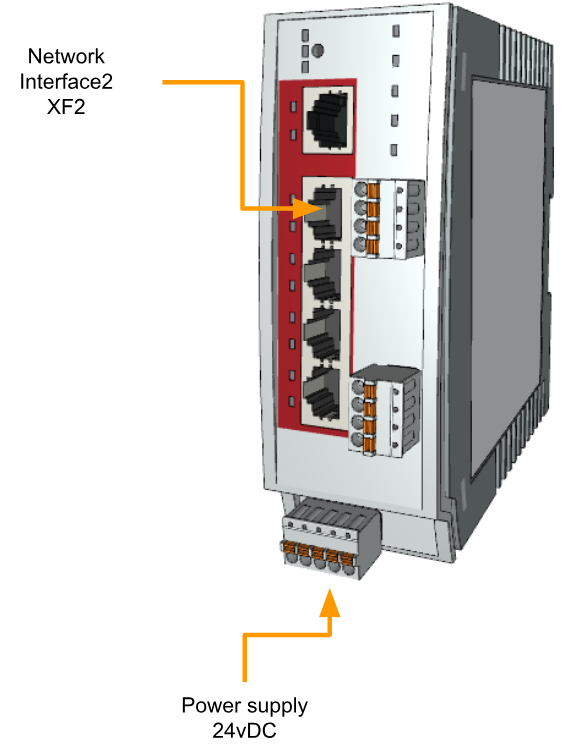
XF2
IP=192.168.1.1, netmask=24.
User access
In the WBM and Config API user interface, the user name and password will return to the Default state.
- User name: admin
- Password private
Start UP!
Now let’s turn on FL MGUARD 1105 and plug the LAN cable into XF2.
Access Web Server
Launch a Browser such as Chrome or Firefox and go to the XF02’s Default IP address https://192.168.1.1にアクセスしましょう.This is the Web server Login screen for FL MGUARD 1105.
By default, Username=admin, Password=private.
Done!I was able to Login to the Web Server of FL MGUARD 1105.
Updating Firmware
First, to update the Firmware of FL MGUARD 1105, please go to Downloads>Firmware>Download from the following side.
https://www.phoenixcontact.com/en-pc/products/router-fl-mguard-1105-1153078
Please accept the Software License and download the update package.
A ZIP file like this was downloaded.
Next, click Management>Firmware update>Update.
Unzip the ZIP file you just downloaded and select the file .update.signed.
Update in progress message will be displayed, please wait a moment…
Done!Firmware has been updated.
2024年12月時点でVersion1.8.0が最新です。
Device access
Management>Device access allows you to restrict access rights to Network Interface 1 and 2.Access rules allow you to limit access to the device’s web server (web-based management or config API) to one of the available netzones.When enabled, access to the device’s HTTPS server is allowed from the selected netzone (TCP port 443).
Time and date setting
Next, go to Management>Time and Date and set the time for FL MGUARD 1105.
Since we did not prepare an NTP Server for this article, we will disable the time synchronization function of the NTP Server.
Instead, click the Calendar button next to the Set time and date Field.
Set the time for FL MGUARD 1105.
Finally, click the button in the red frame to save the settings.
Done!FL MGUARD 1105 hours have been changed.
Network Interface
This time, to change the Network Interface settings for FL MGUARD 1105, click Management>Interfaces. set Net zone1 and Net zone2 to match your actual application.
DHCP Server
You can enable or disable the DHCP Server feature on the FL MGUARD 1105 under Management>DHCP Server.