Here is a new article series using Phoenix Contact’s Security Router FL MGUARD 1105!Cyber security is one of the essential issues in our FA industry today.In Episode 3, I will discuss 1-to-1 NAT and how to set it up.
Come on, let’s enjoy FA.
Reference Link
http://soup01.com/en/category/phoenixcontact/fl-mguard-en/
Reference Video
Phoenix Contact.Open box with FL MGUARD 1105!!
Cybersecurity…
In the previous article, we briefly listed security related to PC Pace software; in this article, we will discuss security related to components that ensure functional safety.When using components that ensure functional safety, it is necessary to implement security measures to ensure functional safety.
Recommendation
In addition, the following basic requirements should be considered and evaluated within the scope of the threat analysis
- Integrity for operations
- Confidentiality according to generally accepted procedures
- Availability of machines and systems, including safety features
It is important to note that functional safety may be compromised by unauthorized access to the network or the device’s communication interface. Safety functions may be unintentionally or intentionally damaged or manipulated.
NAT
The IP addresses of clients on the real network are translated according to 1:1 NAT rules, and communication with clients on the other (translated) network is done via the translated IP address, not the real IP address.
Thus, the real (primarily private) network remains hidden from the network participants of the other (primarily public) network.
Configuration1
The actual IP address (machine control system (PLC) in the production network) is hidden from the network participants in the office network.It communicates with the office network via a translated IP address (e.g., 192.168.1.100 < -> 10.1.0.100).
ARP requests from the office network via the translated IP address will be answered by the mGuard device as representative.
Configuration2
In real-world applications, the same IP configuration is often used in different production cells for connected machines, which leads to address conflicts.
To solve this problem with 1:1 NAT, the device replaces each network portion of the real client IP address in the production network with the network portion of the office network subnet.
For example, 192.168.1.0/24 < -> 10.1.1.0/24. Clients in the office network and production network can now communicate in both directions.
Security…?
While NAT can provide some level of security by hiding internal IP addresses from external networks and hiding network topology, it should not be considered a comprehensive security solution. NAT primarily provides a basic level of protection by preventing direct access to individual devices on the local network from the outside. However, it cannot encrypt data, authenticate users, or protect against sophisticated attacks.
For enhanced security, NAT should be used in conjunction with other security measures such as firewalls, VPNs, and intrusion detection systems to provide stronger protection against unauthorized access and cyber threats.
Firewall
Data packets passing through the device are analyzed by the firewall (packet filter) and forwarded or blocked according to the configured firewall rules.
The FL MGUARD 1105 firewall works on the principle of Stateful packet inspection.
That is, response packets to a request in one direction will automatically pass through the firewall after being allowed by the firewall if they are clearly related to that request. Thus, information about each data connection is stored in a connection tracking table, compared with the response packet, and clearly associated with the corresponding request.
It is important to note that firewall rules do not apply to response packets.
How Firewall can be used in Industrial?
Next, let’s take a look at where Firewalls fit in on Factory Automation.Firewalls are an integral component of an industrial network security infrastructure, providing a first line of defense against external threats and playing a key role in protecting sensitive operations and data. Firewalls should be integrated with a comprehensive security strategy that includes endpoint protection, intrusion detection systems, and regular security audits to ensure robust protection.
✓Protection of critical infrastructure
In industrial environments, firewalls are essential to protect critical systems and infrastructure from cyber threats, preventing unauthorized access to industrial control systems (ICS), SCADA systems, and other sensitive platforms.
✓network segmentation
Firewalls can be used to segment industrial networks into different parts and separate systems based on functionality and security needs. This segmentation limits the spread of potential threats and facilitates management of network traffic.
✓Remote monitoring and management
Firewalls can manage secure remote access to industrial systems, allowing control and monitoring of operations from different locations without compromising security.
✓Data Protection and Compliance
Firewalls help ensure data integrity and compliance with industry regulations by controlling the flow of data and preventing sensitive information from leaving the network without authorization.
✓Protection against malware and attacks
Firewalls play a key role in defending against various types of cyber attacks, including malware, viruses, and denial-of-service (DoS) attacks, by filtering traffic that may contain malicious content.
Start it!
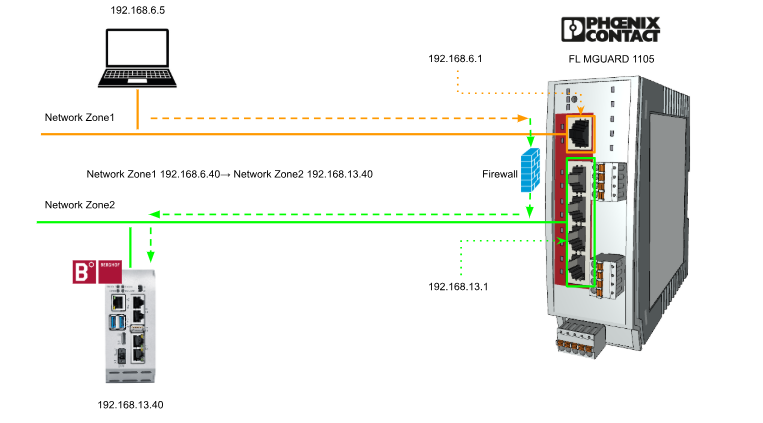
Now let’s set up a 1-to-1 NAT network configuration with Phoenix Contact’s Security Router FL MGUARD 1105.In the figure below, Network Zone 1 (OFFICE area) contains my PC and is connected to XF1 of FL MGUARD 1105.And in Network Zone2 (OT area), Berghof’s Raspberry Controller will be located.
I will now access Berghof’s Raspberry Controller Web Server and Codesys Runtime on my own PC.
Configure Interface
The first step is to configure the Interface settings for network zones 1 and 2.
Access the FL MGUARD 1105 Web Server and configure Interfaces>Interfaces> Net zone1 and Net zone2 IP address settings and other settings to match your actual application.
Network Mode
This article will use the 1:1 NAT feature, so set Interfaces>Interfaces>Mode to Router.
We will be setting up Stealth mode in the future!
Configure Table
The next step is to add the 1-to-1 NAT configuration table to FL MGUARD 1105.
Click on the NAT Tab to configure Port forwarding and 1:1 NAT.Here is a brief explanation of NAT settings.
Add Row to add a new rule to the Table.
New rules have been added to the 1-to-1 NAT Table.
IP Masquerade
In this configuration, Net Zone 2 will be Masquerade, so set the Radio button for Zone 2 to On.
Real IP/network
Data traffic sent from or to network clients on the real network follows 1:1 NAT rules.
1:1 NAT rule: 192.168.1.0/24 <-> 10.1.0.0/24
⇒ Translation: 192.168.1.100 <-> 10.1.0.100
⇒ Translation: 192.168.1.200 <-> 10.1.0.200
The settings in that table allow clients on both networks to communicate in both directions. At the same time, the actual (primarily private) network is invisible to the other (primarily public) network:
- Each translated client IP address of the real network appears as a sender address to the network participants of the other network.
- To reach a client on the real network from the other network, it is necessary to use its translated IP address.
- ARP requests to translated client addresses in the real network are automatically answered by the device they represent.
It is important to note that both the real network and the converted network must be on the same subnet mask.
In this article, the 1-to-1 NAT configuration is set up to convert 192.168.13.40 to 192.168.6.40, so if my PC in Network Zone 1 wants to access Berghof’s Controller, the IP address that my PC should access is 192.168.6.40.
Translated IP/network
Translated IP/network is the network to which the real IP address of the client on the real network will be translated.Note that both the real network and the translated network must be in the same subnet mask.
In this article, the 1-to-1 NAT configuration is set up to convert 192.168.13.40 to 192.168.6.40, so if my PC in Network Zone 1 wants to access Berghof’s Controller, the IP address that my PC should access is 192.168.6.40.
Result
Done!The settings in this article are designed to convert 192.168.6.40 to 192.168.13:40.
Save
Finally, save your settings.
Firwall Setting
To establish one-to-one NAT communication, a firewall must be configured to allow packets from any IP address to pass through and to block packets from any IP address.
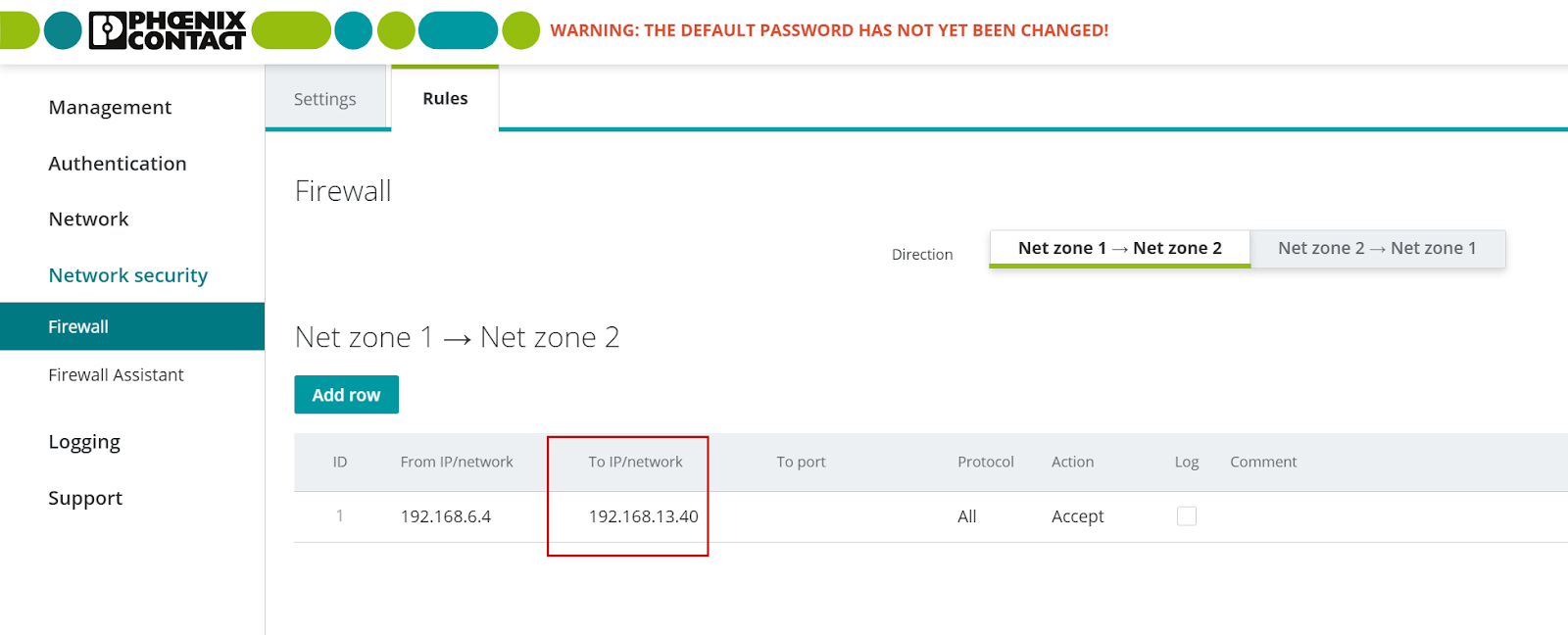
Click Firewal>Rules.
Direction
Firewall rules are set up in two different tables, depending on the direction of the initial data traffic:
- Net Zone 1 → Net Zone 2
- Net Zone 2 → Net Zone 1
Also, depending on the setting of that rule, the status of Packets passing through will change.
- If no firewall rules are configured, all data packets will be dropped.
- If none of the configured rules are applied, all data packets are dropped.
- If one rule is configured and applied, the rule is applied and the configured action is performed.
- If multiple rules are configured and applied, the rules are queried from top to bottom until a rule is found that applies.
Add Rules
Add row to add a new firewall rule.
From IP/network
Set the source (network or IP address) of the data packet for this rule to apply.Note that if “0” is specified as the subnet mask, the rule applies here to all sources (all IP addresses and networks).
To IP/network
Set the destination (network or IP address) of the data packets so that this rule is applied.Note that if “0” is specified as the subnet mask, the rule applies here to all sources (all IP addresses and networks).
 To port
To port
The Port setting will only be available when TCP or UDP is selected as the “Protocol”.Let’s set the destination port or port range to which data packets must be sent so that the rules apply here.
Protocol
TCP, UDP, ICMP, GRE, ESP, All
Configure the network protocols required to send data packets so that this rule is applied.Note that All = all protocols.
Action
Sets the action to be taken when all parameters set in the access rule are applied to the packet.
- Accept: Allow the data packet to pass through.
- Reject: Reject the data packet and notify the sender.
- Drop: Drops the data packet, but does not notify the sender.
Result
Done!Accessing 192.168.6.40 on a PC in the IT area, I was able to access the Berghof Controller’s Web Server.
Next, add a new Gateway to access the Berghof Controller’s Codesys RunTime.
Select the Gateway you have just set up.
Click on Scan Network.
Select that Berghof Controller.
Done!
Of course, you can also download, upload, and monitior projects!