Here is a new article series using Phoenix Contact’s Security Router FL MGUARD 1105!Cyber security is one of the essential issues in our FA industry today. In Episode 4 we will discuss Stealth mode and how to set it up.
Come on, let’s enjoy FA.
Reference Link
http://soup01.com/en/category/phoenixcontact/fl-mguard-en/
Reference Video
IEC 62443
Corporate security is rooted in two worlds: IT (information technology) and OT (operational technology).To protect these two worlds, an information security management system (ISMS) compliant with ISO27001/2 has been implemented in IT and must now be expanded to OT.
ISMS requirements include both technical and organizational requirements; with IEC 62443-2-1, technical requirements can be referenced to measures for OT, Industrial Automation Control Systems (IACS) environments.Therefore, consider IEC 62443 as a supplement to the ISO 27001 standard.
The combination of these two standards provides a comprehensive approach to protecting against cyber threats; measures described in the IEC 62443 series include
- Network configuration and segmentation
- Data protection during storage and transmission
- User authentication
- Monitoring and logging of user and system actions
- Enhanced security of devices in use
- Organizational requirements for managing configuration, update, backup, and restore systems
defense-in-depth…
A special element of IEC62443 is its comprehensive security-by-design approach, which describes both procedural and technical measures and requirements, ranging from requirements for operating processes to requirements for systems and products.
One of the key security concepts of IEC 62443 is “defense-in-depth,” which creates a more difficult situation for attackers by layering multiple security mechanisms one after another.
For example, to launch an attack via the network, an attacker first has to get past one or more firewalls before reaching the target component.Then they have to overcome user logins, which are thwarted by internal security mechanisms.
✓Business Level
At the corporate level, the following measures can be taken;
- Physical measures
- Authentication concepts (entry, admission, access)
- Awareness training
- ISMS Process
✓network level
The following measures can be taken at the network level
- Network segmentation (zone, conduit)
- VPN
- Encryption
- Firewalls
- Attack detection
✓Product Level
The following measures can be taken at the product level;
- Security Features
- System Robustness
- “Security by Design” component
360° security concept
Phoenix Contact began implementing IEC 62443 in 2017, establishing the 360° security concept and putting into practice the guiding principle that “security is entrenched throughout the lifecycle of our products and solutions”.In this article, we will look at Phoenix Contact’s approach to security.
✓Security Development Process
A security development process compliant with IEC 62443-4-1 is a prerequisite for the development and the complete life cycle of a product.It not only defines development in accordance with established cybersecurity practices – security-by-design and defense-in-depth – but also ensures vulnerability monitoring and regular security updates.
✓Security Products
Security products are developed according to the 4-1 development process and meet the functional security requirements in the following system configurations For example,
- Protection against DDoS attacks (Distributed Denial of Service)
- User management
- Confidentiality of data in transit
- Storage
In 2021, PLCnext Control is a controller certified according to the IEC 62443-4-1 ML3 / 4-2 SL2 feature set, and other security products are currently under development or certification.
✓✓PLCnext Control:IEC 62443 certified safety and security
As part of the 360° security concept, PLCnext Control is a TÜV SÜD certified controller according to the IEC 62443-4-1 ML3 / 4-2 SL2 feature set.
This certification was further extended in 2022 with the continued addition of PLCnext Controls and the addition of the PLCnext Control family of functional safety devices.
PLCnext Control’s IEC 62443 certification includes extensive security features:
- Security profiles as minimum functional settings
- Firewall, network segmentation, network load monitoring and limitation
- TLS security for access secure communication
- Certificate management for asymmetric encryption and key management
- User management, role-based local administration, connection to central user management system
- Event logging system with local and central connections
- PSIRT automatically monitors known vulnerabilities of software components in use and issues security advisories.
- Central management of devices for security updates (firmware and applications), device and update management apps as backup and restore management
✓✓mGuard Security Routers
The mGuard Security Routers used in this series offer comprehensive security features that strongly protect industrial networks from unauthorized access and malware.Proven mGuard security technology controls and protects communications within a machine or production network.This product is part of Phoenix Contact’s comprehensive 360° security concept.
Industrial routers are developed according to a certified development process in accordance with IEC 62443-4-1 ML3 and feature extensive security features.There are intelligent firewalls with various functions depending on the application.
- Conditional Firewalls
- DNS Name Based Firewall
- User Firewalls
- Firewall Redundancy
- Routers with NAT and 1:1 NAT
- IPsec VPN capability
- Certificate-based
- Switchable via I/O
- Local and centralized (RADIUS) user management configuration
- Local and centralized security logging
- NTP: Network-wide time synchronization
- Device and update management via mGuard Device Manager
- System usage notifications
PLCnext Control’s cyber security can be complemented systemically by mGuard technology.Depending on the system’s application and risk analysis, additional devices can be used for segmentation, additional firewalls, or security via VPN (e.g. remote maintenance or cloud access).
The interaction of both solutions results in the overall protection of the system or machine network.
✓Security services
The team must possess and demonstrate appropriate cybersecurity skills in order to discuss, advise, install, and maintain security solutions with system integrators and operators.Phoenix Contact also has a team certified in accordance with IEC 62443-2-4 and is your expert security consultant.
✓Security Solutions
Templates (blueprints) are developed for different solutions and markets and certified according to IEC 62443-3-3 as required.They demonstrate Phoenix Contact’s expertise in solution certification, including facilitating discussions and concept work.
✓PSIRT
The Product Security Incident Response Team (PSIRT) is the central team tasked with responding to potential security vulnerabilities, incidents, and other security issues related to Phoenix Contact’s products, solutions, and services.
The PSIRT manages disclosures, investigations, internal coordination, and publishes security advisories regarding identified vulnerabilities.All of their certifications are monitored by an annual audit by TÜV SÜD.
Example
This is a “Remote Monitoring and Control” design drawing certified by TÜV SÜD in accordance with IEC 62443-3-3.
Stealth mode
Stealth Mode is used to protect one or more local clients in an existing subnet (e.g., Controller/IO in a production network) from unwanted network access without changing IP settings. To do so, the device is added between the client and the surrounding subnet via two network interfaces (netzones) and all data traffic to and from the client is routed through and monitored by the device.
No changes to the network configuration of the connected clients are required.Server services DHCP, NTP, SNMP, and DNS servers are stopped on the device.Device security and firewall features are typically applied to incoming and routed data traffic.
Factory automation can play a key role in enhancing the security of industrial control systems (ICS) such as SCADA (supervisory control and data acquisition) systems, PLCs (programmable logic controllers), and other critical manufacturing systems.
✓Packet filtering and response control
Devices in Stealth mode do not respond to unauthorized network traffic.For example, if an outside entity attempts to scan the network for open ports, the firewall will ignore these requests rather than responding with a “closed” or “filtering” message.This lack of response makes it difficult for an attacker to determine which services or devices are active.
✓Enhanced Security
By hiding network services and devices, stealth mode helps protect critical systems from reconnaissance activities commonly used by attackers to gather information before attempting an attack.
✓Limiting Information Exposure
Stealth mode limits the amount of information that is disclosed to the outside world.Instead of revealing port status and device presence, it effectively creates a “hiding” effect, making the network less attractive to attackers.
Stealth mode mechanism
✓IP Address Hiding:
Firewalls can be set to Stealth mode to prevent certain IP addresses from being recognized by external network scans.This means that the IP addresses of critical devices remain hidden from direct access attempts.
✓Blocking ICMP Requests:
In Stealth mode, ICMP echo requests (e.g., ping commands) can be blocked.This means that if an attacker tries to ping the device to see if it is alive, there will be no response.
✓Non-Response to Connection Attempts:
Devices in Stealth mode simply do not respond to connection requests instead of indicating whether the port is open or closed.
Example of Stealth mode usage
✓Protection of critical infrastructure
In environments where critical infrastructure is running (e.g., SCADA systems in industrial environments), an additional layer of protection against external cyber threats can be added.
✓Improvement of security posture
Organizations seeking to strengthen their overall security posture can deploy Stealth mode on their firewalls and security devices to deter attackers and reduce the risk of successful reconnaissance.
✓Regulatory Compliance
Certain industries are required to meet compliance standards, including strict security measures; leveraging Stealth mode can help meet these regulatory requirements.
✓Deterrence against reconnaissance attacks
Cyber attackers often conduct reconnaissance to find vulnerabilities in the network; Stealth mode reduces visibility of network devices, making it difficult for attackers to gather information about the system, such as which services are available and which devices are onlineWhat services are available, what devices are online, etc.
✓Enhanced network segmentation
In factory automation, it is important to segment the network into individual zones (for production, management, etc.).Stealth mode enforces this segmentation by allowing only authorized devices to communicate with each other, preventing potential cross-network attacks.
✓Monitoring and Alerts
While operating in Stealth mode, the network security device can monitor traffic patterns and log unauthorized access attempts.Suspicious activity can be alerted and acted upon quickly without revealing the device’s presence.
Limitations of Stealth mode
It is important to know the limitations of all features as well: while Stealth mode offers significant benefits with respect to security, it is not a stand-alone solution; Stealth mode hides certain elements of the network, but it does not encrypt data or prevent any form of attack (It cannot encrypt data or protect against all forms of attacks (e.g., DDoS attacks).
Start it!
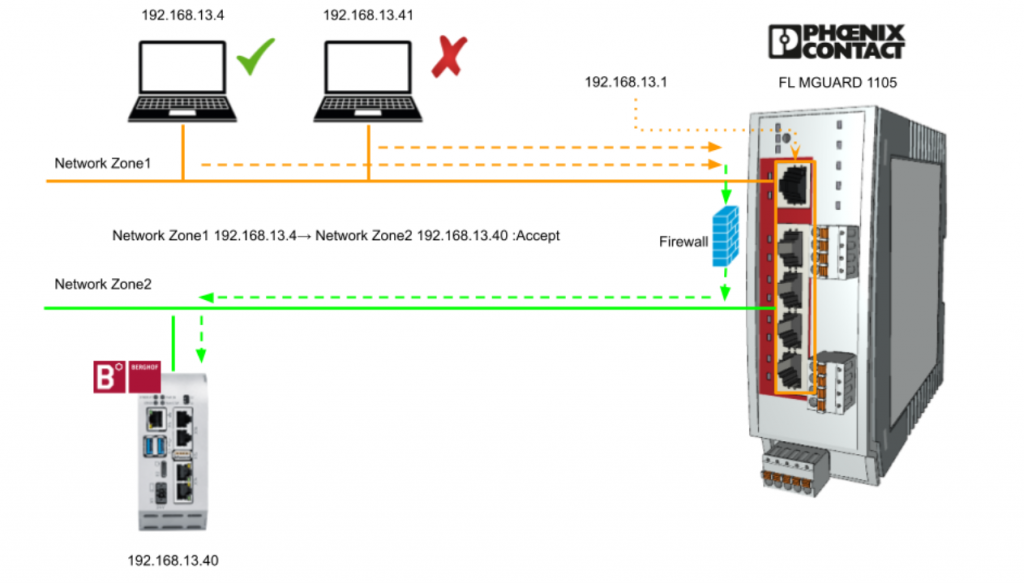
Now let’s set up the Stealth mode configuration on Phoenix Contact’s Security Router FL MGUARD 1105.In the figure below, Network Zone 1 (OFFICE area) contains my PC and is connected to XF1 of FL MGUARD 1105.And in Network Zone2 (OT area), Berghof’s Raspberry Controller is located.
I will now access Berghof’s Raspberry Controller Web Server on my own PC.
Configure Interface
First configure the network interface of Phoenix Contact’s Security Router FL MGUARD 1105.
Go to the Web Server of Phoenix Contact’s Security Router FL MGUARD 1105 and set it to Interfaces>Interfaces>Stealth.
The screen changes to Management IP address setting only, so set the IP address according to your application.
Its Management IP address will be the IP address at which the device is reachable and manageable in stealth mode.Its Management IP address is available on all network interfaces (netzones).
It is important to note that if you change the IP address currently used to access the device, the device will no longer be available at this address after the configuration is saved.Please log in again with the changed IP address.
Firewall
The next step is to configure the Firmwall settings.In this example, we will restrict access to 192.168.13.40 only to the IP address 192.168.13.4.
From the Web Server of Security Router FL MGUARD 1105, open the Firwall>Rules tab.
Add Rules as shown below.
The Rules we just added have been configured to allow access to 192.168.13.4->192.168.13.40.
This time, we also want to record the access log of the device, so let’s put in the Check Box for Log and save the settings.
Result
Finally, set your PC’s IP address to 192.168.13.4 to access the Berghof Controller’s Web Server.
The Logging screen also keeps a history of successful Packages passage.
Next, change the IP address of the PC and try to access the Berghof Controller’s IP address 192.168.13.40 one more time.
As shown in the figure below, 192.168.13.41 is not configured as passable in the Firmwall rules, so naturally the request cannot reach the Berghof Controller.